A Fresh New Hydra Head
Since Brian Krebs broke with the news about the merger between ZeuS and SpyEye, many security vendors have argued whether this information is true or just a rumor.
Some of the vendors have uncovered “hard evidence” of cyber criminals posting on underground forums about this new merge. These posts were later found to be fake.
A week ago, Trend Micro Labs described what seemed to be the real SpyEye administration panel of the merged malware kit. Recent findings by Seculert Research Labs uncover that this may just be the tip of the iceberg. In fact, our researchers found that this piece of “Hydra” malware has a fresh new ZeuS head.
As of today, ZeuS still keeps the crown as the king of botnets, with thousands of different malware kits being bought and installed by cybercriminals. Those cybercriminals are used to the clean bluish interface of the Zeus administration panel, and therefore will find it easier to work with the new SpyEye/ZeuS merged version.
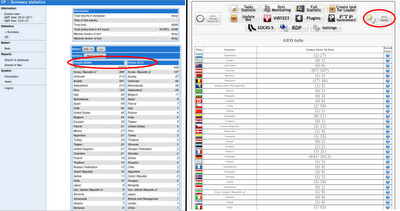
As you can see in Figure 1, the new merged kit contains “SpyEye-like” and “ZeuS-like” administration panels. Both are connected to the same backend database, showing the same botnet statistics.
Typically, ZeuS names each bot using the following convention:
COMPUTER_NAME_UNIQUEID.
For example: LAPTOP_SMITH_AB5D3E79.
SpyEye uses a different naming convention for its bots:
USERNAME/OS_VERSION!COMPUTER_NAME!UNIQUEID.
For example: 5.1.2600!LAPTOP_SMITH!AB5D3E79.
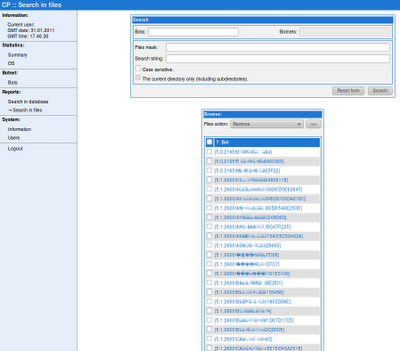
Figure 2 shows a “search in files” page from the ZeuS side of the admin panels. However, the naming convention of the bots is exactly like SpyEye.
In addition, the files (which are actually certificates being stolen from the botnet victims) are stored in the database, exactly as SpyEye stores files. ZeuS, on the other hand, saves those certificates as files on the server.
This version of the Zeus/SpyEye merge seems to be in the midst of a serious development effort, and its version number (1.3.05b) indicates that it’s indeed still in beta testing.
Much like with the old versions of ZeuS and SpyEye, conventional security solutions will find it hard to detect and handle this type of new threat. This is exactly where a pinpointed threat intelligence service can help.
Figure 1 – Both panels of Zeus / SpyEye Hydra merge
Figure 2 – ZeuS panel of the ZeuS / SpyEye merge showing SpyEye bot names
Is your network compromised? Take a free trial of Seculert and discover threats your other security solutions have missed.
>>Much like with the old versions of ZeuS and
>>SpyEye, conventional security solutions will
>>find it hard to detect and handle this type of
>>new threat. This is exactly where a pinpointed
>>threat intelligence service can help.
The key sentence here.
Question (and not a rhetorical one): Do you think that if the US Congress issued a Letter of Marque and Reprisal to a licensed and bonded cyber privateer, and tasked that privateer to loot the bad guys, that the bad guys would think twice before plying their trade? In other words, is there a deterrent value?
Finding a C&C server that is running both a Zeus and SpyEye control panel does not make it the “true” hybrid. Gribo only gave out the builder, SpyEye server control panel, VMware image for server, server files, and plugins. He never gave out the zeus control panel to go along with the new SpyEye. I think you are making incorrect assumptions here.
Do you think that if the US Congress issued a Letter of Marque and Reprisal…
No, there’s no deterrent value. Simply because there’s no way to reach through the screen and put a gun in the face of the bad guys. And what are you going to loot? They don’t actually carry any “treasure” themselves, they sell the info they collect to someone else.
I don’t think you understand the scope, here? This isn’t a few Blackbeards. This is several thousand criminals, all operating under their own rules, with a complete economy and in some cases even a form of government.