The New Trend in "Malware Evolution"
Back in the days when malware was more about fun and less about profit, the talk about “Malware Evolution” was very simplistic. These discussions focused mainly on the new client side features of the malware and how it behaves on the infected machine.
Today, the malware authors are all about profit, and they are doing everything in their power to make their malware as stealthy as possible. This means trying to dodge common end-user security products (e.g., anti-virus), as well as evading security products that monitor the network traffic. For these reasons, it’s time to start using new terms when discussing “Malware Evolution”.
Rootkits are probably the most common feature in today’s “Malware Evolution.” In the case of rootkits, the malware abuses several operating system (OS) features in order to go undetected by both the OS itself and end point security solutions.
However, now that malicious code in the wild is getting updated and being controlled from remote cybercrime servers, the malware authors are also determined to remain invisible to network security products like firewalls, intrusion prevention systems (IPS), etc. which monitor network traffic.
Carberp as a case study
Let’s take the Carberp information stealing Trojan as an example. Many pundits speak of Carberp as the eventual successor to ZeuS in the realm of botnets.
In terms of network traffic, the first known version of Carberp started with a simple server side PHP script (task.php, first.php). The malware installed one plug-in (grabber.pcp) which was used to steal information. The stolen information was then sent to the Carberp drop server in clear text.
The next version of Carberp was a bit more complex. An htaccess file was used to redirect requests to specific HTML filenames (task.html, first.html) to one PHP server side script which handled all the botnet tasks. This version of the malware installed several plug-ins:
1) stopav.plug – Anti-Virus killer
2) miniav.plug – Removes other malware from the infected machine (much like the ZeuS killer feature that was introduced by SpyEye)
3) passw.plug – Information stealer
The stolen information was still sent in clear text.
Carberp evolves
Recently, Seculert Research Lab identified what seems to be a new version of Carberp. This new version includes several interesting new features:
1) Network traffic evolution: All communications with the Command & Control (C&C) server, as well as the stolen information sent to the malware drop, are encrypted using RC4. The interesting part is that the RC4 key is randomly generated and is sent as part of the HTTP request. This is the first time we have encountered such behavior. For example, other malware, such as ZeuS, only use one RC4 key which is embedded within the malware itself.
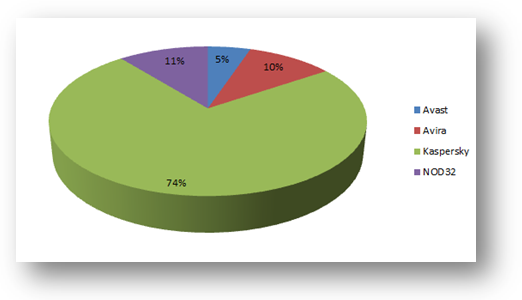
2) Anti-Virus statistics: While the new version of Carberp sends information about the running processes on the infected machine to the C&C server, as in previous versions, it now also checks which AV software is installed on the machine (see screenshot below). The following pie chart shows the distribution of different AV products which are installed on a specific botnet’s infected machines. The majority of the victims are using Kaspersky. This is probably because this botnet primarily targets people from Russia.
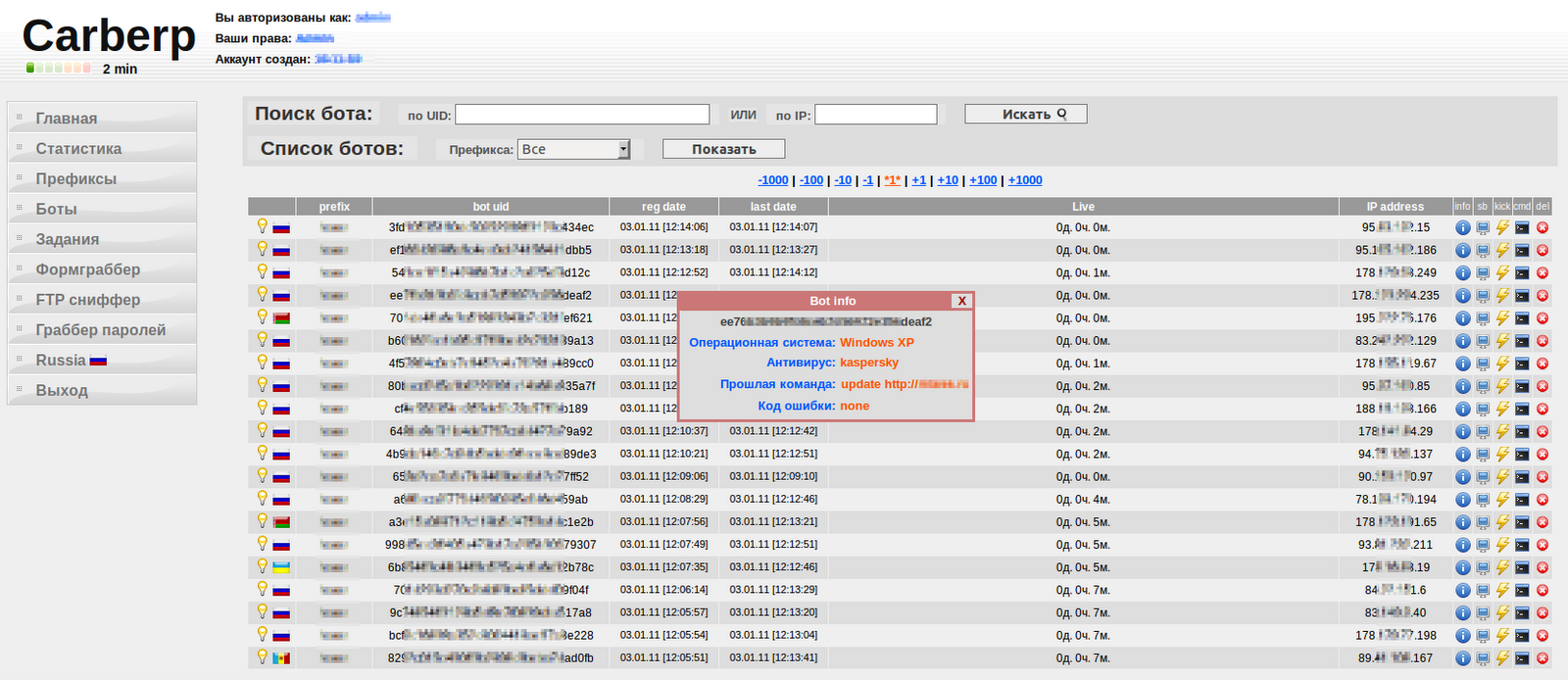
3) Malware name: Previous versions of Carberp didn’t seem to use this name, neither in the malware code nor in the administration panel. As you can see in the screenshot below, the name “Carberp” is mentioned in the logo of the new version’s Administration Panel. We suspect that the authors of this malware have embraced the security industry alias for this piece of malicious code.
Based on the “success” of Carberp, we expect to see other types of malware evolve similarly with respect to the way they communicate with Command & Control servers and the nature of information they collect about their victims.
It’s time that the security industry confronts this new type of “Malware Evolution” and starts to think out-of-the-box (literally) about malware detection and prevention.
Is your network compromised? Take a free trial of Seculert and discover threats your other security solutions have missed.
It is a nice blog. I dont know what to say except that I have enjoyed reading. Nice blog.
Nice read. I am eager to analyse this behavior. Could you please share the Sample’s details? (MD5?)
How can you detect if you have been compromised by Carberp? Microsoft’s Malicious Software Removal tool does not seem to support this yet.
Hi Steve, Seculert’s cloud-based service will detect systems in your network compromised by Carberp and other botnets.
Actually this article helps me a lot as documentation for my work.It’s interesting how it can generate a random RC4 key? How the C&C knows this key generated by the malware in order to decrypt the traffic?
“..RC4 key is randomly generated and is sent as part of the HTTP request..”
Try reading first, before asking silly questions. It can also be generated from ANY http-send data, as both cnc and bot know this data
################################################
“..Microsoft’s Malicious Software Removal tool does not seem to support this yet”
You really think Microsoft will help you protect the system? Trust me, it won’t.
This isn’t a real Carberp panel, is a modified version of Carberp. This version is only attacking russian systems, and the new panel hasn’t the name of Carberp and have new options like RDP of SpyEye.
regards,
how is encrypting and sending the key any evolution? its basicly the same as using a fixed hardcoded key… if ur product had trouble facing this “evolutin”, your really in bad shape…
Toll free numbers are ideal for small business and entrepreneurs. It gives a professional image and make sure that you don’t miss a single call. Few years back, I decided to buy toll free numbers from Telcan. You can get more information here: Toll Free
this is one of the awesome posts. I like your blog details.
Thanks
this is one of the awesome posts. I like your blog details.
Thanks
When the internet found its way into people’s homes and offices en masse in the mid-1990s, it was widely regarded as beneficial, giving people access to information — and each other — in a way that was previously impossible
I am using windows 7 home premium (64-bit) original OS. Its windows defender is updated and working nicely. Should I also download & use extra anti-malware or windows defender is enough to fight against malware?