Exploit Kits as a Service
The cybercrime ecosystem has often been compared to the legitimate business world.
In fact, as the business world advances, we also see the cybercrime ecosystem taking similar steps – sometimes “copying” business models and trends.
A salient example of one such business model is the highly popular “Software as a Service” (SaaS) or “Cloud-based” software solutions.
Like many other vendors, Seculert recognized the opportunities and the progress in the SaaS realm and designed its cyber threat management solution as a cloud-based service.
Recently, Seculert Research Lab discovered that cybercriminals have also adopted the use of “cloud-based” solutions, and now offer their own “customers” (other cybercriminals) a SaaS solution for hosting and managing exploit kits and malware installs. We have dubbed this trend “Exploit Kits as a Service”.
Instead of purchasing hosting services, a domain and the exploit kit itself, the “customer” pays a monthly fee for an account which covers all of the above. There is no need for separate purchasing and no software needs to be installed. This also eliminates the hassle of managing the removal of their hosting or domain by ISPs, registrars or law enforcement agencies (see recent Rustock case).
Exploit Kit as a Service – Incognito 2.0
The first version of the Incognito exploit kit was actually a rip of an exploit kit called “Fragus”. The authors simply copied the kit, changed the name and modified the look-and-feel (logo, colors, etc.).
A few months ago, Seculert Research Lab identified a new version of this exploit kit – Incognito 2.0. This version includes mostly the same exploits as the previous version. However, it now has a new “cloud-based” administration interface (Figure 1).
Over a two-week period in the middle of January 2011, our researchers identified over 30 different customers (Figure 2) that used the Incognito 2.0 Exploit Kit as a Service to automatically install different variants of the following malware families:
• ZeuS
• Fake AV
• Gbot
• Optima DcyDOS botnet
• Ransomware
• Trojan Downloader
Recently, one of the Incognito customers was using a spam campaign which disguised itself as a “Twitter Support Message”, encouraging recipients to click on a link to view a “VIDEO: Inside the Fukushima’s exclusion zone”. Naturally, the link did not display the video but rather installed a Trojan Downloader on the victims’ machines.
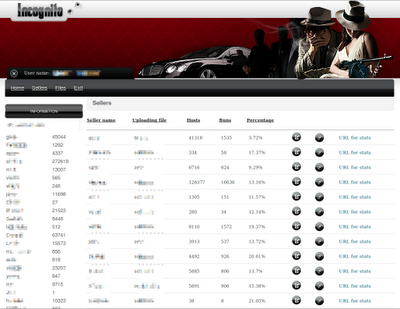
Figure 2: Incognito 2.0 Exploit Kit as a Service customers list,
including hosted malware files and infection (“runs”) statistics
During this two-week period alone, Seculert researchers were able to identify over one million visitors, from over 8,000 hacked websites (Figure 3), which were redirected to the Incognito crime servers. Over 150,000 of those visitors were automatically infected with one of the malware families mentioned above. Almost 70% of the infections exploited an unpatched Java Runtime Environment, while 20% were due to an unpatched version of Adobe Reader (Figure 4).
Any Incognito customer can easily use the exploit kit as part of an Advanced Persistent Threat (APT) attack – much like what was probably done with the attack on RSA. Now, with the availability of this “cloud-based” exploit-kit-as-a-service, these attacks have become easier, stealthier and more affordable for cybercriminals. This trend is another important reason why organizations should consider using a pinpointed threat intelligence service, which can help with the detection and mitigation of such threats.
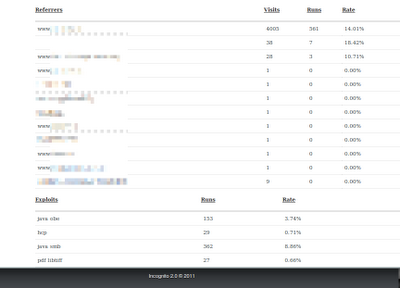
Figure 3: One of the Incognito 2.0 customer’s list of
hacked websites, being redirected to the crime server
Is your network compromised? Take a free trial of Seculert and discover threats your other security solutions have missed.
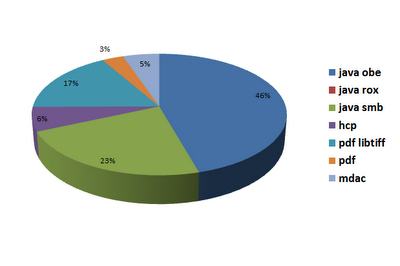
always surprising to see the MDAC exploit is still alive and kicking.
Please don’t obfuscate bad IPs or domains. The bad guys already know them; the good guys don’t.
“Please don’t obfuscate bad IPs or domains. The bad guys already know them; the good guys don’t. “
+1
Well, this isn’t a new market… Bomba works with this idea, and Blackhole also has this solution from developers..