SpyZeus Evolves
Two months ago we published a blog post with findings related to the merge of SpyEye and ZeuS. Today, Seculert Research Lab would like to report a new development in the evolution of the SpyZeus malware.
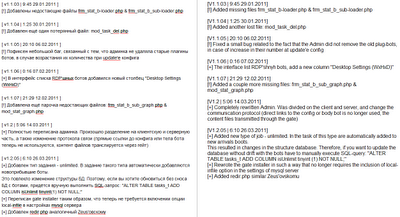
Examining the SpyZeus administration panel “Release Notes” (Figure 1), we can identify two major updates:
• Rewrite of the administration panel
• Communication protocol change
Rewrite of the Administration Panel
Evidently, the malware author has decided to focus his efforts on rebuilding the “SpyEye-side” (Figure 2) of the administration panel. Thus, it is reasonable to assume that most of the cybercriminals using this malware kit have chosen to adopt this side of the SpyZeus administration panel.
The latest versions of SpyZeus reconstruct the admin panel, and further differentiate the admin panel files from the Command and Control gate PHP file.
Moreover, the SpyZeus admin can now view the Remote Desktop screen resolution of the victim’s machine, as well as being able to set tasks for the bots without time limits.
Communication Protocol Change
Until recently, the communication protocol between the SpyZeus malware bot and the Command and Control (C&C) server was almost exactly as in the old SpyEye versions – i.e., clear text. Some of the data was also sent via the HTTP request query string. This made it easier for network security monitoring solutions to identify traffic which belonged to an infected machine.
Example: http://spyeye.com/gate.php?guid=5.1.2600!COMP-HOME121245!12318D8D&ver=10309&ie=7.0.5730.13&os=5.1.2600&ut=Admin&ccrc=D123D7BC&md5=3a1d1c123c2893e64d3123b65f95db&plg=customconnector&stat=online
SpyZeus is a modular malware, which means that anyone with the right programming skills can develop plug-ins for SpyZeus and sell them to cybercriminals. Some of the known plug-ins include a credit-card grabber, FTP credentials stealer and even a DDoS module (known to be used for DDoS attacks on SpyEyeTracker). One of the most recently developed plug-ins is called SecureConnect, which allows the malware bot to encrypt its communication with the C&C server, using a very simple XOR algorithm.
Recent versions of the SpyZeus malware bot have started to use a similar encryption communication protocol, which is fully integrated within the malware out of the box (Figure 3).
As of today, our researchers have seen the following SpyZeus bot versions using this integrated feature in the wild:
• v1.03.026
• v1.03.032
• v1.03.033
Since XOR is a very simple encryption algorithm, we believe that some of the network monitoring solutions should be able to deal with this level of encryption. However, much like the Carberp malware evolution, we suspect that the SpyZeus encryption will be much stronger in future versions, probably similar to the encryption algorithms used in ZeuS. Therefore, enterprises should consider adding a pinpointed threat intelligence service to their current security solutions arsenal.
In addition to the new encryption feature, SpyZeus has also introduced an option to redirect traffic, similar to that used in ZeuS
Is your network compromised? Take a free trial of Seculert and discover threats your other security solutions have missed.

SpyZeus?? xDD This is the new panel of SpyEye, not SpyZeus…. and this panel have a month…