by Aviv Raff on | Leave a comment
Filed under Research Lab and tagged Advanced persistent threats (APT), Botnet, Targeted attack.
Filed under Research Lab and tagged Advanced persistent threats (APT), Botnet, Targeted attack.
During the past week a clash has been going back and forth between the two security vendors, Kaspersky and McAfee, with regard to “Operation Shady RAT“.
The main issue between the two was how much of a threat this attack is actually is, and at the center of it was the question whether Shady RAT is an “Advanced Persistent Threat” (APT) or a Botnet.
Firstly, let’s try to understand what an APT is and what botnet is and then evaluate Operation Shady RAT to see if it’s either of these.
Usually, when referring to a threat as an APT, it means that the main part of the attack is targeted to a specific individual, a group of people, a company, or a state.
From McAfee and Symantec reports we can clearly deduce that Operation Shady RAT is indeed a targeted attack on specific companies worldwide. Several of the attacks were persistent and some of them were spread over 2 years. The entire operation lasted at-least 5 years.
On the other hand, a botnet is a network of infected machines, controlled by either an individual, or a group via at least one Command & Control (C&C) server.
Again, from the reports it is obvious that there are dozens or even hundreds of organizations which were infected by Shady RAT, all of which were controlled by the same C&C server, using the same method of communication.
Seculert has developed a free online tool, called Shady RAT Checker, where you can easily determine whether a machine, using an IP address of your company, was communicating with the Shady RAT C&C server.
As you can conclude from the above facts, both McAfee and Kaspersky are correct. Operation Shady RAT is an APT which utilizes a botnet infrastructure to manage the attack. However, unlike most of the botnets, the risk of Shady RAT is a function of its targets, rather than of its size.
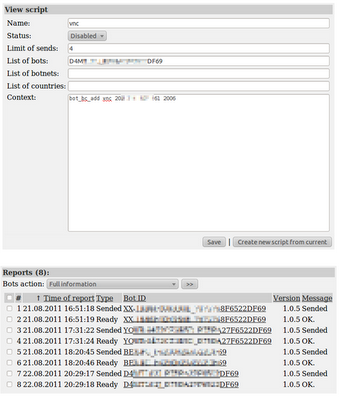
Operation Shady RAT is not the first botnet which is also a targeted attack. Seculert monitors – on a daily basis – hundreds of botnets which use specific scripts to attack predetermined targets, either individuals or companies (Figure 1).
These targeted threats are becoming more common every day, and they expose the inadequacy of traditional security products to protect corporate assets. In order to better detect and mitigate these kinds of threats, an enterprise should add a pinpointed threat intelligence service to its current security solutions arsenal.
Is your network compromised? Take a free trial of Seculert and discover threats your other security solutions have missed.