MSUpdater Trojan and the Conference Invite Lure
This blog post is based on a joint report by Seculert and Zscaler (blog post). Researchers from both companies separately identified attacks which used a Remote Access Tool (RAT) malware, and recently targeted several government-related organizations. With joined forces, our researchers analyzed the incidents and were able to link them to previous government-related targeted attacks that have been occurring since early 2009.
Seculert and Zscaler identified similar command and control (C&C) beacon patterns. The most often observed are HTTP GET requests to the path:
/microsoftupdate/getupdate/default.aspx?ID=[num1]para1=[num2]para2=[num3]para3=[num4]
The malware attempts to stay under the radar of network security products by sending fake “Microsoft Windows Update” HTTP requests. Another malware participating in these attacks dropped a file named “msupdater.exe“. Therefore, we have decided to refer to this threat family as the “MSUpdater” Trojan.
Seculert’s FogSense Cloud-Based Service observed instances of these same malicious patterns for our customers as early as March 2010. By correlating this information with additional Open-Source Intelligence (OSINT) and matching the domain registration info of some of the C&C observed (for example, siseau.com, vssigma.com, etc.), we linked the new “MSUpdater” Trojan to previous attacks, probably conducted by the same group. Additional similar parameters and further technical details about the MSUpdater Trojan and previous attacks can be found in the report.
A noteworthy targeted attack became unintentionally public, following one of last year’s many data breaches. It was a spear-phishing attack which targeted a US based global defense technology company. The infection vector was an email sent on Sept. 23rd, 2010, with a conference invitation and a malicious attachment – “ISSNIP_2010.pdf” (See Figure 1 and 2). ISSNIP is an international conference series on Intelligent Sensors, Sensor Networks and Information Processing. Clearly, it is a highly targeted attack on that global defense technology company. The attachment allegedly exploited Adobe Reader vulnerabilities and dropped a few executable files, among which is “msupdater.exe”.
It appears that the usage of emails with conference invitations that contain malicious attachments (mostly PDF files) is growing, as we identified several spear-phishing attacks started using this method.
Attackers are trying to lure employees of specific organizations with “invitations” to relevant industry conferences. In addition to ISSNIP, we have seen malicious invitations to an IEEE Aerospace Conference, an Iraq Peace Conference and more.
The targeted attacks identified by Seculert and Zscaler, which share a few similar technical parameters (thus, regarded as created by the same group of attackers) arrive in emails with a malicious PDF attachment, mostly related to a conference in the targeted industry. The PDF exploits, at that time, 0-day vulnerabilities within Adobe Reader and executes series of malicious files in a sophisticated manner.
Please note that if your organization encounters this type of advanced threat, it will most likely be persistent and bound to exist undetected for a long period of time in your network, as well as most probable to happen again in the future.
Seculert and Zscaler’s joint report mission is to inform security executives about these threats, and assist them in adapting their organizations’ security policies and resources.
FogSense, a new cloud-based service from Seculert, thoroughly scans your log files, detecting unexposed malware and advanced threats affecting your company’s assets, and utilizing Big Data analytics to identify targeted attacks over a long period of time.
Join our beta and easily find out whether your organization is affected by similar
advanced threats!
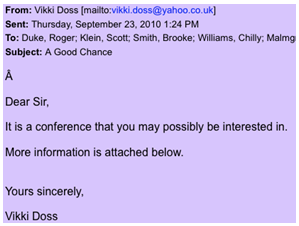

I am amused to find our conference poster (ISSNIP 2010) being used as an attack vector. One of our conference sponsors was the US Office of Naval Research. That may explain why.
Receiving a PDF file from an unknown person using a Yahoo account should have raised an immediate concern in the mind of any security conscious person. At least checking the message header would have been an extra minimum