Ramnit Goes Social
Much has been written about the Ramnit worm and its transformation into a financial malware. And now, Seculert’s research lab has discovered that Ramnit recently started targeting Facebook accounts with considerable success, stealing over 45,000 Facebook login credentials worldwide, mostly from people in the UK and France.
Discovered in April 2010, the Microsoft Malware Protection Center (MMPC) described Ramnit as “a multi-component malware family which infects Windows executable as well as HTML files”, “stealing sensitive information such as stored FTP credentials and browser cookies”. In July 2011 a Symantec report [PDF] estimated that Ramnit worm variants accounted for 17.3 percent of all new malicious software infections.
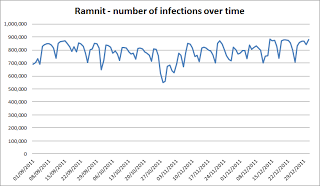
In August 2011, Trusteer reported that Ramnit went ‘financial’. Following the leakage of the ZeuS source-code in May, it has been suggested that the hackers behind Ramnit merged several financial-fraud spreading capabilities to create a “Hybrid creature” which was empowered by both the scale of the Ramnit infection and the ZeuS financial data-sniffing capabilities. This synergy has enabled Ramnit to bypass two-factor authentication and transaction signing systems, gain remote access to financial institutions, compromise online banking sessions and penetrate several corporate networks. With the use of a Sinkhole, we discovered that approximately 800,000 machines were infected with Ramnit from September to end of December 2011.
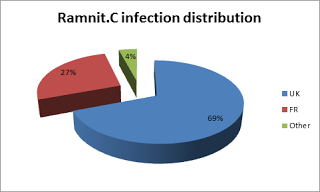
It seems, however, that this is not the last twist. Recently, our research lab identified a completely new ‘financial’ Ramnit variant aimed at stealing Facebook login credentials. Since the Ramnit Facebook C&C URL is visible and accessible it was fairly straightforward to detect that over 45,000 Facebook login credentials have been stolen worldwide, mostly from users in the United Kingdom and France.
We suspect that the attackers behind Ramnit are using the stolen credentials to log-in to victims’ Facebook accounts and to transmit malicious links to their friends, thereby magnifying the malware’s spread even further. In addition, cybercriminals are taking advantage of the fact that users tend to use the same password in various web-based services (Facebook, Gmail, Corporate SSL VPN, Outlook Web Access, etc.) to gain remote access to corporate networks.
With the recent ZeuS Facebook worm and this latest Ramnit variant, it appears that sophisticated hackers are now experimenting with replacing the old-school email worms with more up-to-date social network worms. As demonstrated by the 45,000 compromised Facebook subscribers, the viral power of social networks can be manipulated to cause considerable damage to individuals and institutions when it is in the wrong hands.
* Seculert has provided Facebook with all of the stolen credentials that were found on the Ramnit servers.
Is your network compromised? Take a free trial of Seculert and discover threats your other security solutions have missed.
OMG , shockin truth ! Now I need 2 strengthen up my security layer … before I end up as a victim .
Will this affect my Debian Linux system or do only the Windows users need to be concerned ?
How does one know if one’s account has been affected?
Oh gosh guys, just don’t click at incoming links and everything is gonna be fine.
reading the microsoft statement; this only affects users stupid enough to use internet explorer or people that open word/excel files and allow macros to be run.
Bottom line; use more professional software and you are fine.
>> In addition, cybercriminals are taking advantage
>> of the fact that users tend to use the same
>> password in various web-based services (Facebook,
>> Gmail, Corporate SSL VPN, Outlook Web Access,
>> etc.) to gain remote access to corporate networks.
Then you deserve it to be hacked
To say “then you deserve to be hacked” is like saying the weak, the ill, the poor, all deserve their miserable lives. If not for the people who don’t know better how to use technology but want to try, the rest of us who DO know how, would not have an audience to care about what we do.
@brainpower
full ack
thanks
“… this only affects users stupid enough to use internet explorer…”
Nope, this only affects people stupid enough to use the internet and feel they are magically exempt because they have not yet been targetted. “First they came for…and I did nothing. Then they came for…”
Linux has no viruses – just use Elinks browser (it’s the new Lynx) and you will be safe.
“Linux has no viruses”
I laughed
never use facebook ,but how do you know if you are victim thats been infected for those who use facebook users to know,,,,,,
te-bay.blogspot.com/2011/12/facebook-porn-video-virus-remedy.html#axzz1iC5VcBNy
I am a malware analyst and currently analyzing Ramnit worm as per you wrote, so far we received Ramnit samples and is not related to the facebook at all.
Please share me your sample, as we can share ours to you.
You may reach me in twitter/blogger/Virus Total as I am using same handle name anywhere.
Looking forward.
- @unixfreaxjp – Malware Analyst http://unixfreaxjp.blogspot.com
thanks for this good information about blog posting, I agree with the importance of niche for the blog postings……… keep update us………..
Hey, There, I found your blog while surfing the web. This is a really well written article. I’ll be sure to bookmark it and come back to read more of your useful information. Thanks for the excellent post. I will certainly return. sesli chat
This is very alarming issues. Please let us know how can we
identify this kind of malware.
Firstly if you cannot open your AV homepage or any AV Site thats an indication you are infected (DDOS).I used Malware (ANTI MALWARE) on top of what I had. This software detected Ramnit twice on my computer but I have been able to recover the PC. its free for 30 days but doesnt effect performance and has excellent capture rate I also used a symantec anti root kit software just to contain the virus. I also used PC Tune up to get rid of any broken files. Standard AV does not cut it you have to protect yourself vigilintly. The virus is very agrressive.
Very interesting article. Content has been written in very nice manner. I enjoy reading this kind of stuff. Thanks for sharing good knowledge.
Internet security has become most important thing that people look for in business as it protect our income source from criminals so I think we should protect our business with the help of a expert.
The blog is really informative and i like to share it with my friends. Got a lot of information from this post. Please give us some more news. Thanks for your post in fact it is an excellent post.
Internet security must quickly close off new threats such as mobile device management and BYOD companies policies