Kelihos.B is still live and social
Kelihos was a botnet which operated in 2011, infecting over 40,000 PCs at its peak. It shared a large amount of code with the infamous Waledac botnet, a fact which suggested that perhaps it was created by the same group, or as some sort of dubious cybercriminal collaboration.
Kelihos was shut down by Microsoft (together with Kaspersky and Kyrus Tech) in September 2011 in an operation codenamed “Operation b79″.
This operation included filing a lawsuit against a Russian citizen, Andrey Sabelnikov, accusing him of operating Kelihos, and a complaint against the owners of the domain cc.cz, in which Sabelinkov allegedly registered 3700 sub-domains, used to operate and control the Kelihos botnet. Brian Krebs mentioned that some sources believe Sabelnikov was not the only person behind Kelihos, but was instead only a developer. Microsoft’s operation terminated Kelihos’ activity almost completely. In February 2012, Microsoft estimated that there were less than 10,000 infected computers in the inactive botnet.
Later on that month, it was reported that the Kelihos botnet had raised its head again, and with greater power. Researchers discovered new variants of Kelihos, using advanced features. Microsoft quickly informed the public that the original Kelihos botnet was still dead, and although the new botnet uses very similar code to the old Kelihos, it is a different version of the malware – “Kelihos.B”
Several weeks ago, Seculert discovered that Kelihos.B had found a new and “social way” to expand, using an already-known social worm malware, but now it had started targeting Facebook users.
In April 2011, security researchers warned of a malware which was spreading via Facebook. This malware sent all the victim’s friends a message which directed them to a URL with a photo album download link (See Figure 2), and this actually downloaded a malicious file (back then this was a Fake Antivirus software). The malware continued to spread, as it was able to create a dummy blog at Blogger.com and redirect more traffic to it using the goo.gl URL-shortener.
Kelihos.B is currently using the same photo album worm to spread their own malware via Facebook (See Figure 1). This may bring back questions about the identity and the origin of the Kelihos botnet and recent trends of collaboration between cybercriminal groups.
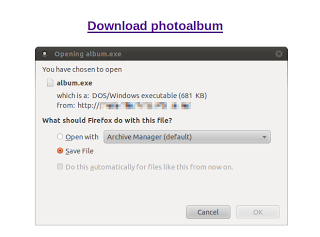
Figure 2: Clicking the malicious link shows a “Download photoalbum” message which downloads Kelihos.B
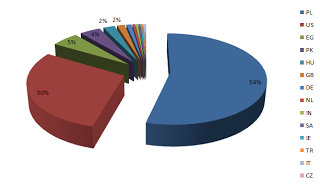
Up to now Seculert has identified more than 70,000 Facebook users that are infected with the Facebook worm, and sending the malicious links to their Facebook friends. Most of the infected machines are from Poland (54%) and the United States (30%).
Seculert has provided Facebook with all the relevant information gathered.
Yesterday, researchers from CrowdStrike and Kaspersky reported that they have used a sinkhole to try and shutdown the Kelihos.B botnet, and according to Kaspersky’s blog they did that with great success.
Unfortunately, at the time of this writing, Seculert can still see that Kelihos is being spread using the Facebook worm. Also, there is still communication activity of this malware with the Command-and-Control servers through other members of the botnet. This means that the Kelihos.B botnet is still up and running. It is continuously expanding with new infected machines, and actively sending spam.
Some might call this “a new variant”, or Kelihos.C. However, as the new infected machines are operated by the same group of criminals, which can also regain access to the sinkholed bots through the Facebook worm malware, we believe that it is better to still refer this botnet as Kelihos.B.
Is your network compromised? Take a free trial of Seculert and discover threats your other security solutions have missed.
It was a widespread case in the UK as it targeted so many affiliate sites and job hunting sites such as umbrella companies in uk where the IT companies quickly cleansed it with a bot sweep.