Mahdi – The Cyberwar Savior?
“In Islamic eschatology, the Mahdi is the prophesied redeemer of Islam who will rule for seven, nine or nineteen years before the Day of Judgment and will rid the world of wrongdoing, injustice and tyranny. In Islam Ahmadiyya, the terms “Messiah” and “Mahdi” are synonymous terms for one and the same person.” — Wikipedia
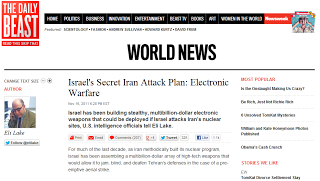
Several months ago, Seculert stumbled upon an interesting, yet simple, spear-phishing attack. Our Research Lab had identified a suspicious email which included a fake word document attachment. Opening the attached file executed a malware dropper, and a “mahdi.txt” file which contained and opened a real word document. The content of the document was an article discussing Israel vs. Iran electronic warfare (see Figure 1).
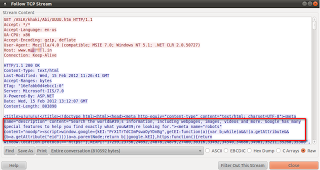
To determine where the attack originated, Seculert’s Research Lab began examining the malware communication with the command-and-control (C&C) server. Interestingly, we found that the communication, and several of the server-side components, included strings in Farsi as well as dates in the Persian calendar format (see Figure 2).
Mahdi disguises the communication between the malware and the C&C server by delivering updates and modules (See Figure 3), such as information stealing, audio recording and keylogging, via a legitimate-looking Google web page. The actual module code is base64 encoded and hidden within the HTML of the Google-like web page (See Figure 4).
The variant we examined communicated with a server located in Canada. We were able to track variants of the same malware back to December 2011. Back then, the malware communicated with the same domain name, but the server was located in Tehran, Iran.
In May of 2012 Kaspersky Lab announced that they had discovered a highly sophisticated, malicious program that is actively being used as a cyber weapon to target entities in several countries. Named Flame, the malware was designed to carry out cyber espionage and is believed to exceed the complexity and functionality of other known attacks.
We contacted Kaspersky Lab in order to investigate possible similarities between Flame and Mahdi. We collaborated in the weeks that followed, with Kaspersky keeping a close eye on how the malware affected infected endpoints and Seculert analyzing the communication between the malware and the C&C servers. By using a Sinkhole and Seculert’s big data analytics technology, we were able to identify over 800 victims, communicating with four different C&C servers over a period of eight months.
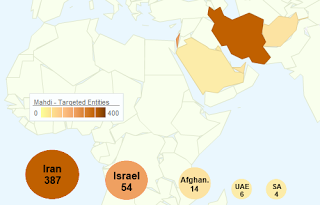
While we couldn’t find a direct connection between the campaigns, the targeted victims of Mahdi include critical infrastructure companies, financial services and government embassies, which are all located in Iran, Israel and several other Middle Eastern countries (See Figure 5).
It is still unclear whether this is a state-sponsored attack or not. The targeted organizations seem to be spread between members of the attacking group by giving each victim machine a specific prefix name, meaning that this operation might require a large investment and financial backing.
We will continue to monitor Mahdi and update this blog on our findings. For more information on Kaspersky Lab’s research, visit Securelist blog.
Is your network compromised? Take a free trial of Seculert and discover threats your other security solutions have missed.
So was it a .txt file or a word file or the word file was “inside” the txt. anyone?
Mahdi does not mean Messiah.
Messiah is مسیح
whereas Mahdi means Guide. The Guide will come WITH the Messiah at the end of the world.
They basically come together according to Iranian Shiah theology but are not the same person. In Ahmadiyya theology this was the one and same person i.e. an Ahmad who appeared in the 19th century. But there are no Ahmadis in Iran. They only exist in what is now Pakistan.
You’re absolutely correct!
That was a real bother back then. It disrupted a lot of devices that were handling the crucial financial and business systems and almost threatened to cause a major dent in the economies concerned. Good thing it didn’t go that far.