New Mahdi updates, new C2 server
Like any other software, malware goes through revisions and updates.
But unlike legitimate software, malware needs to change its update servers much more frequently.
Take Mahdi, for example. When Seculert first spotted Mahdi, in February 2012, the variant of the malware communicated with a command and control (C&C) server in Canada. After further research, we found a different variant in December 2011 that communicated with the same domain name, but at the time the domain resolved to an IP address located in Tehran. A month later, the same domain name resolved to the IP address of the same server we spotted in February.
As part of our joint research with Kaspersky Labs, we identified different variants, with different versions of the malware, communicating with four additional servers all located in Canada. While most of the variants communicated with these four servers, a new variant was recently found that communicated with a fifth C&C server located in Canada as well.
After investigating the fifth server, we discovered that there are different malware variants communicating with it dating back to June 2012 and it seems to have replaced the original server that we spotted in February 2012. Interestingly enough, since June, it was able to successfully target over 150 new entities worldwide. While most of the targeted entities are from Iran, some of them seem to be located in the US and Germany. This correlates back to the fact that the latest version of Mahdi, added new triggers to the malware – “USA” and “GOV”.
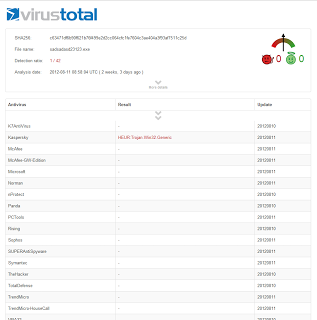
In the past few weeks we were able to monitor dozens of new variants of the Mahdi malware. Many of these variants are not being detected by most AV vendors (see Figure 1) and it looks as if the group behind Mahdi is testing new and improved versions of the malware in order to find new ways to evade detection by security vendors.
Is your network compromised? Take a free trial of Seculert and discover threats your other security solutions have missed.