It’s a Kind of Magic Persistent Threat

People sometimes compare the malware world to a form of magic. You don’t really know how the magic is done, or how eventually your network or system has come to be controlled by an adversary.
“Every great magic trick consists of three parts or acts. The first part is called “The Pledge”. The magician shows you something ordinary: a deck of cards, a bird or a man. He shows you this object. Perhaps he asks you to inspect it to see if it is indeed real, unaltered, normal. But of course… it probably isn’t. The second act is called “The Turn”. The magician takes the ordinary something and makes it do something extraordinary. Now you’re looking for the secret… but you won’t find it, because of course you’re not really looking. You don’t really want to know. You want to be fooled. But you wouldn’t clap yet. Because making something disappear isn’t enough; you have to bring it back. That’s why every magic trick has a third act, the hardest part, the part we call “The Prestige“.”
– from the movie, “The Prestige”
The Pledge
Recently, we had a malware sample uploaded to Seculert Swamp that I would call one of “The Pledge” samples that we see. The sample got flagged due to a behavior that seemed a bit out of the ordinary for a legitimate executable. Usually, when a malware initiates a communication with a C2 server, the first response is a setting, telling the malware what to do next.
The Turn
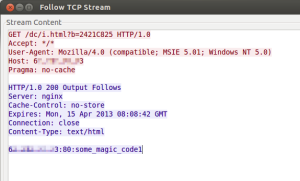
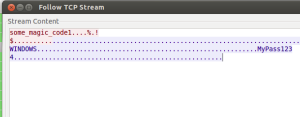
“The Turn” for this bit of malware magic was that the response was a bit strange. The C2 server told the malware to start communicating with the same IP address and port. But from then on, instead of using the HTTP protocol, the malware had to communicate with the C2 server using a custom-made protocol, and always using a magic code at the beginning of the conversation (See Figure 1). In one case, as shown in Figure 2, the malware is asking the C2 server, using the custom-made protocol, what to do. The C2 server responds with a command to add a new backdoor user — Username: WINDOWS, Password: MyPass1234 — which enables the attacker to remotely access the infected machine or network.
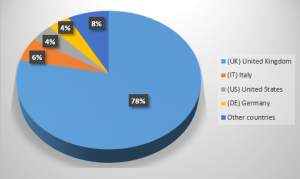
This “magic malware” — as we’ve dubbed it — is active, persistent and had remained undetected on the targeted machines for the past 11 months. Since then the attackers were able to target several thousands of different entities, most of them located in the United Kindom (See Figure 3).
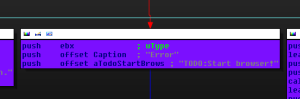
Furthermore, this persistent threat is still under development. We have seen several indications of features which are not yet implemented, and functions which are not yet used by the malware. For instance, in case the attacker would like to open a browser on the victim’s machine, the malware will popup on the RDP session for the attacker a box with the message: “TODO:Start browser!” (See Figure 4)
The Prestige
The real intention of the attackers behind this magic malware, their third act, “The Prestige”, is yet to be known. As the malware is capable of setting up a backdoor, stealing information, and injecting HTML into the browser, we believe that the current phase of the attack is to monitor the activities of their targeted entities. But, because this malware is also capable of downloading and executing additional malicious files, this might be only the first phase of a much broader attack.
For more information about this attack and other persistent threats, please leave a comment or contact us.


Thanks for article!
What you named malware sample?
Can you please provide MD5′s?
You know, if you’re going to release a security article about a new threat, at least have the common decency to give it a specific identifier that other articles will use like Virus.VB.DK or Worm.Bumdoc, not “Magic Malware”. Due to these generic terms it makes it hard to search for information on it or for virus identification databases to index it , not to mention allows article writers use deceptive titles such as ‘The new “Magic” trick’ which don’t clearly state their subject matter. Just my two cents.
This blog post needs more details to be of any interest. Magic values in c2 and using port 80 to bypass firewall restrictions is pretty standard. Any type of fingerprinting info for the c2 would be useful for defensive actions on a network.
Any chance of getting SHA1s or MD5s of the threats? Makes cross-referencing from a blog post significantly easier!
MD5s, C2 servers and other IOCs can be found on the Magic Malware FAQ blog post.